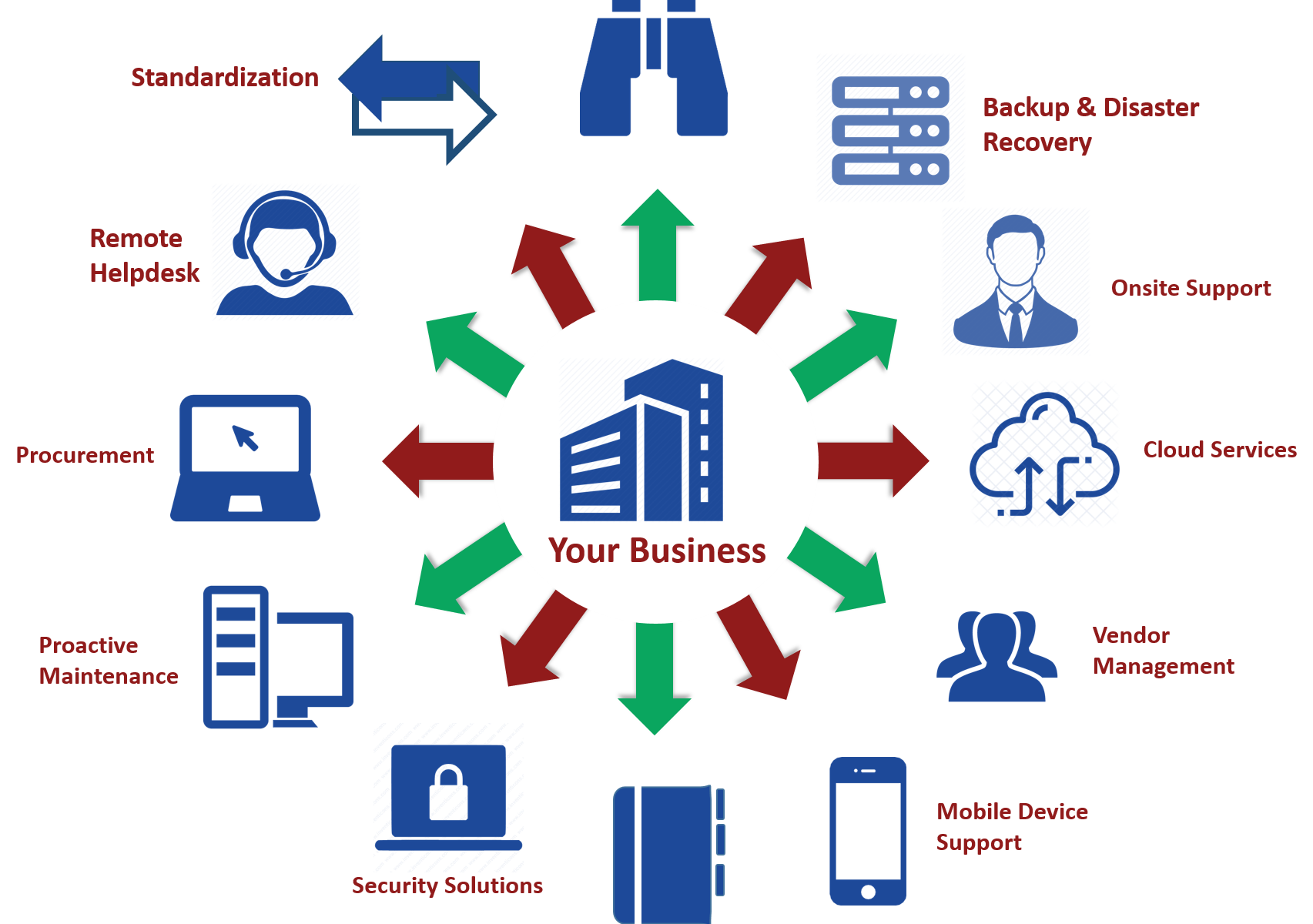
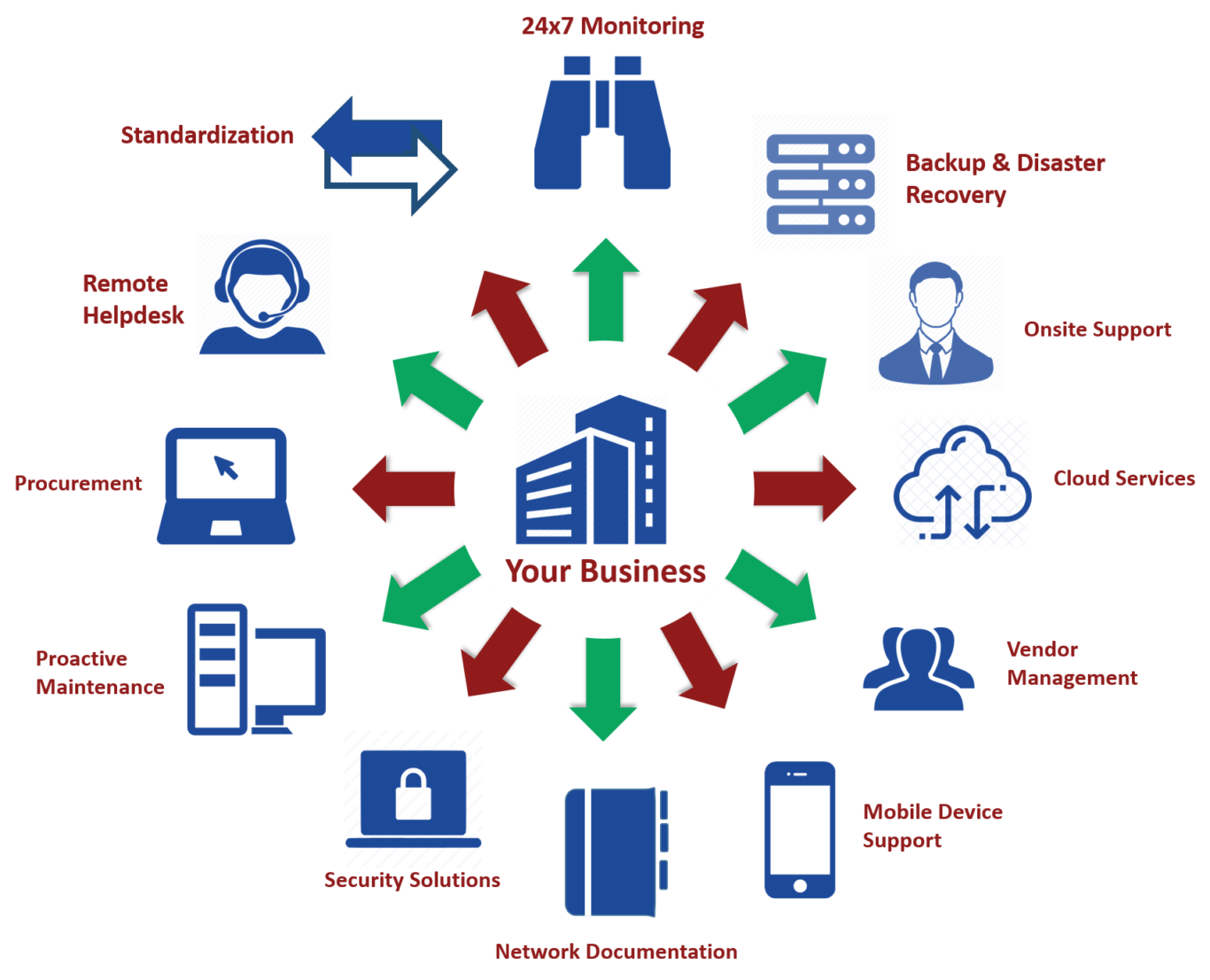
As a SMB owner, you likely wear many hats and juggle multiple responsibilities on a daily basis. From managing finances and operations to marketing and sales, there is always something on your plate. It can be overwhelming, especially if you’re trying to do everything on your own.
That’s where managed services come in. A managed service is a third-party company such as Danush that provides a range of IT and/or business-related services on a contract basis. These services are designed to help businesses run more efficiently and effectively, while also reducing costs and increasing productivity.
In this blog, we’ll explore the benefits of managed services and how they can be a secret weapon for small and medium business success.
Benefit #1: Cost Savings
One of the biggest benefits of managed services is the potential for cost savings. When you hire a managed service provider like Danush, you only pay for the services you need, rather than paying for an in-house team of IT professionals or business consultants. This can be a significant cost-saving measure, especially for small and medium businesses that may not have the budget for a full-time IT staff.
Additionally, managed service providers often have economies of scale and can offer services at a lower cost than an individual business could on its own. For example, a managed service provider may have access to bulk discounts on hardware and software purchases, which can save your business money.
Benefit #2: Expertise and Support
Another advantage of managed services is the expertise and support you’ll receive. Managed service providers are experts in their field and can provide specialized knowledge and support that may be beyond the scope of your in-house team. This can be particularly beneficial for small and medium businesses that may not have the resources or expertise to handle certain tasks on their own.
For example, if you’re struggling with cybersecurity issues, a managed service provider can provide the necessary expertise to help you secure your systems and protect your business from cyber threats. Or, if you’re looking to implement a new business process or technology, a managed service provider can provide the guidance and support you need to ensure a smooth implementation.
Benefit #3: Improved Efficiency and Productivity
Managed services can also help improve efficiency and productivity within your business. When you outsource certain tasks to a managed service provider, you free up time and resources that can be better used elsewhere. This can help you focus on core business functions and allow you to be more productive and efficient.
Additionally, managed service providers often have the latest tools and technologies at their disposal, which can help streamline and automate certain processes. This can help save time and reduce errors, improving overall efficiency and productivity.
Benefit #4: Scalability
Finally, managed services offer scalability. As your business grows and changes, your needs may change as well. With managed services, you can easily scale up or down as needed, ensuring that you have the resources and support you need to meet your business objectives. This can be especially beneficial for small and medium businesses that may not have the budget or resources to handle large scale projects on their own.
In conclusion, managed services can be a secret weapon for small and medium business success. They offer cost savings, expertise and support, improved efficiency and productivity, and scalability. By outsourcing certain tasks to a managed service provider, you can focus on core business functions, reduce costs, and increase productivity, all while ensuring that you have the resources and support you need to succeed.
How to Choose the Right Managed Services Provider?
When it comes to choosing a managed services provider, there are several factors that SMBs should consider to ensure they select the best provider for their needs. Some key considerations include:
Reputation: It is important to select a provider with a good reputation in the industry. Look for providers that have a track record of success and customer satisfaction.
Services Offered: Make sure the provider offers the specific services that your business needs. Don’t be afraid to ask for references or case studies to see how the provider has helped similar businesses.
Pricing: Consider the cost of the managed services in relation to the value they provide. While it may be tempting to choose the cheapest option, it is important to ensure that the